In this piece, I will analyze the best hardware wallets to secure your crypto assets in 2025. As digital assets skyrocket in value, protecting them from hacks and theft becomes crucial.
- What Is a Hardware Wallet?
- How to Secure Crypto with the Best Hardware Wallets
- How to Secure Crypto with the Best Hardware Wallets – Step-by-Step Example (Ledger Nano X)
- Step 1: Purchase from the Official Source
- Step 2: Unbox and Verify Authenticity
- Step 3: Set Up the Device
- Step 4: Backup Your Recovery Phrase
- Step 5: Install Ledger Live App
- Step 6: Add Crypto Apps
- Step 7: Move Crypto to the Wallet
- Step 8: Verification and Confirmation of Transactions
- Step 9: Update Firmware
- Step 10: Secure Storage and Safe Use
- Top Hardware Wallets in 2025
- Why Hardware Wallets Are Essential
- Offline (Cold) Storage
- Full Ownership of Assets
- Protection from Phishing & Scams
- Defense Against Exchange Hacks
- Advanced Security Chips
- Multi-Currency Support
- Backup & Recovery Options
- Regular Firmware Updates
- Key Features to Look for in a Hardware Wallet
- Secure element or hardened microcontroller
- Offline key generation and storage (cold storage)
- Physical display & buttons for transaction confirmation
- Backup and recovery seed phrase support
- Wide coin/token and blockchain compatibility
- Firmware updates & open security architecture
- Passphrase / extra security layers
- Tips to Keep Your Crypto Safe
- Buy Only from Official Sources
- Never Share Your Recovery Phrase
- Use a Strong PIN or Passphrase
- Store Recovery Phrase Offline
- Update Firmware Regularly
- Avoid Connecting to Unknown Devices
- Verify Transactions on the Device Screen
- Employ Multi-Factor Security
- Common Mistakes to Avoid
- Purchasing From Unverified Sellers
- Saving Recovery Phrase Online
- Ignoring Firmware Updates
- Using Weak PINs or No Passphrase
- Connecting to Infected Devices
- Sharing Recovery Phrase for “Support”
- Not Verifying Transaction Details
- Neglecting Physical Security
- Losing Backup Without Redundancy
- Overlooking Compatibility Before Purchase
- Pros and Cons of Using Hardware Wallets
- Future of Crypto Security and Wallet Technology
- Conclusion
- FAQ
Offline hardware wallets are the gold standard for securely protecting your cryptocurrencies and keeping your keys safe. They provide total control over your assets and privacy.
What Is a Hardware Wallet?
A hardware wallet is a physical device that stores cryptocurrencies securely offline, shielding them from hacking and phishing attacks.
Unlike software or exchange wallets that leave a constant internet connection, hardware wallets keep private keys locked within the hardware, safeguarding full control and ownership over funds.

While performing a transaction, the user connects the crypto wallet to a personal computer or smartphone and verifies it with the included security features, which may include PINs and biometrics.
Well-known examples, Ledger and Trezor, designed encrypted chips and backup seed phrases, positioning them as one of the most secure options for long-term cryptocurrency storage in 2025.
How to Secure Crypto with the Best Hardware Wallets
How to Secure Crypto with the Best Hardware Wallets – Step-by-Step Example (Ledger Nano X)
Step 1: Purchase from the Official Source
Buy your Ledger Nano X directly from the official Ledger website or an authorized reseller to avoid tampered or counterfeit devices.
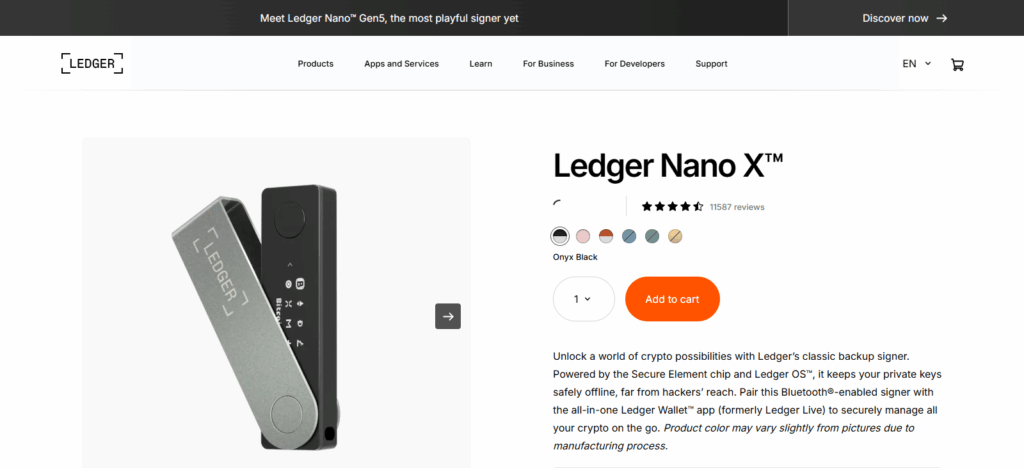
Step 2: Unbox and Verify Authenticity
Check for intact packaging and security seals. Connect the device and verify authenticity through the official Ledger Live app.
Step 3: Set Up the Device
Turn on the wallet and follow on-screen instructions. Create a strong PIN code — this will be needed to access the device.
Step 4: Backup Your Recovery Phrase
Write down the 24-word recovery seed phrase displayed on the screen. Store it offline in a secure, fireproof, and waterproof location — never take a photo or share it online.
Step 5: Install Ledger Live App
Download the Ledger Live app on your computer or smartphone. This app allows you to manage and track your crypto assets safely.
Step 6: Add Crypto Apps
Within Ledger Live, for every cryptocurrency you have (like Bitcoin and Ethereum), you need to install the corresponding app. These apps help you manage that particular blockchain.

Step 7: Move Crypto to the Wallet
Next, you need to transfer the crypto you have to your Ledger wallet address, and you can do this from an exchange or your software wallet. Be careful and confirm that the wallet address is correct.
Step 8: Verification and Confirmation of Transactions
It is crucial to confirm the transaction details on the device screen whenever crypto is sent or received. This is to prevent malware from altering the details.
Step 9: Update Firmware
It is important to update the wallet firmware regularly using the Ledger Live app to ensure you have the latest security updates and features.
Step 10: Secure Storage and Safe Use
When your wallet is not in use, ensure that it is completely disconnected from the internet. The device and recovery phrase should be stored in separate locations to improve security.
Top Hardware Wallets in 2025
Trezor Model T
In 2025, the Trezor Model T stands out as one of the best hardware wallets, attributed to its sophisticated security systems and ease of use.
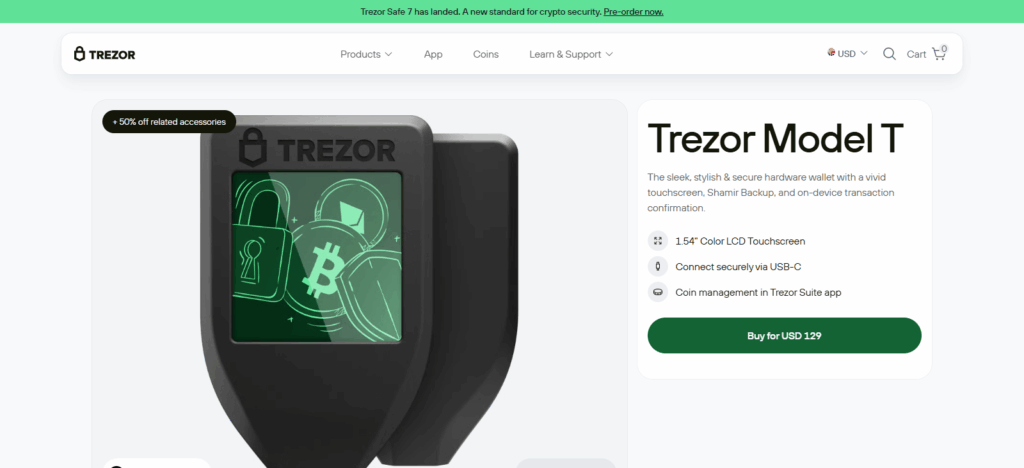
Users validate transactions on-screen, as the hardware wallet incorporates a full-color touchscreen, which also defends against phishing and malware. Its open-source firmware is regularly audits and adds a layer of trust as it is highly commendable in the crypto community.
Also, the Model T is compatible with a variety of cryptocurrencies, wallets, and DeFi systems. Cryptographic storage, PIN locks, and recovery backups balance security, accessibility, and trust, which is all you need in a wallet.
Ellipal Titan 2.0
The ELLIPAL Titan 2.0 stands out from other hardware wallets due to its truly air-gapped design. Without wireless connections to any other devices, ELLIPAL Titan 2.0 is the safest hardware wallet on the market.
While other wallets utilize Bluetooth, WiFi, or USB connectivity, the Titan 2.0 only communicates via QR-code. All information within the Titan 2.0 is 100% secure. ELLIPAL Titan 2.0 makes it especially convenient to travel with your tokens. The Titan 2.0 dual air-gapped design is a patented ELLIPAL feature.
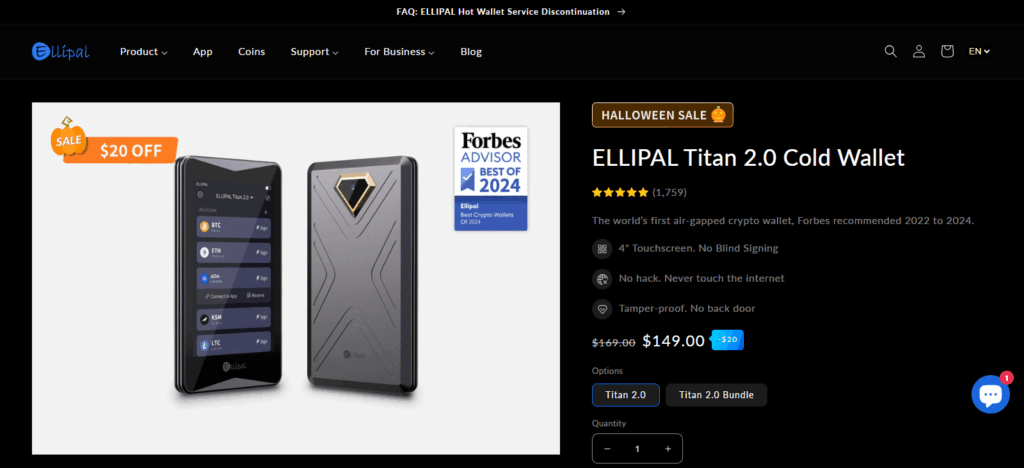
Titan 2.0 is designed to prevent any sort of contact during air-gapped transactions, the wallets outer shell is designed with a self-destruct mode which activates when physical tampering is attempted.
For users serious about maximum security in 2025, the Titan 2.0 is the best option around due to its air-gapped design, tamper resistance, and extensive coin/token variety.
SafePal S1
SafePal S1 is lauded as one of the best hardware wallets available primarily because of its dedication to security and usability. It is also the only hardware wallet with a 100 percent air-gapped design—no WiFi, Bluetooth, USB, or NFC—meaning that your private keys are never exposed to the dangers of an internet connection.
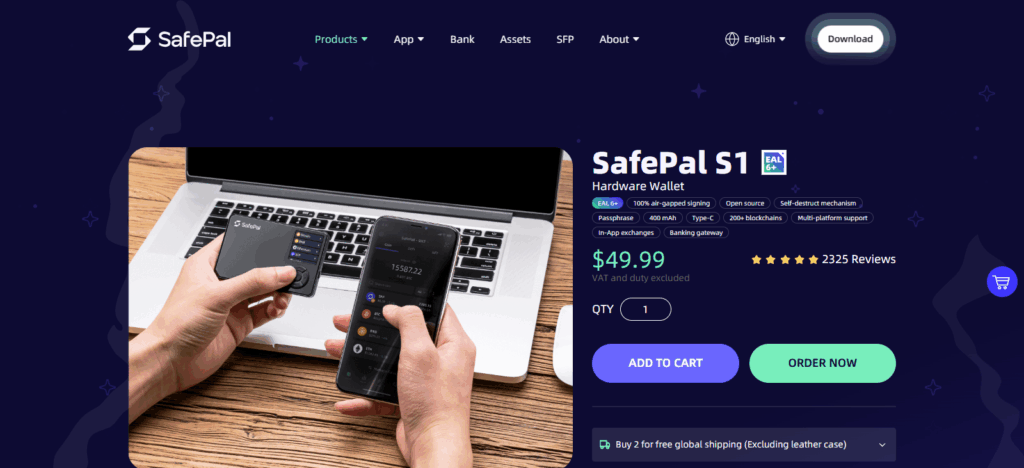
It has top-quality security features, including an EAL5+ (or higher) certified secure element, a genuine hardware random number generator, and a self-destruction feature that renders the wallet unusable if tampered with. .
Furthermore, its small size, low cost, and ability to support a wide variety of blockchains and tokens makes it a truly versatile hardware wallet for 2025 crypto holders.
Why Hardware Wallets Are Essential
Offline (Cold) Storage
Malware and hackers can’t infiltrate your wallet if your private keys are stored offline and in cold storage.
Full Ownership of Assets
You have complete ownership of your crypto without third-party exchanges or custodians.
Protection from Phishing & Scams
Transactions have to be confirmed on the physical device. This means fake websites or apps can’t take your crypto.
Defense Against Exchange Hacks
Even if an exchange is hacked, your crypto is safe, as it is securely stored in your wallet.
Advanced Security Chips
Most modern hardware wallets use EAL5+ secure element chips to prevent physical tampering and key extractions.
Multi-Currency Support
Leading wallets like Ledger, Trezor, and SafePal support hundreds of crypto, currencies, and DeFi tokens in a single wallet.
Backup & Recovery Options
Recovery seed phrases are provided for wallets, so if your device is lost or damaged, you can restore it.
Regular Firmware Updates
These updates are in place to ensure your wallet can’t be compromised with the new cyber threats.
Key Features to Look for in a Hardware Wallet
Secure element or hardened microcontroller
A secure chip that withstands physical attacks and side-channel attacks will protect your private keys.
Offline key generation and storage (cold storage)
Eliminating the risk of hacks occurs when private keys are stored in a wallet that doesn’t connect to the internet.
Physical display & buttons for transaction confirmation
The malware on your computer cannot fool you into sending funds if you confirm the transaction on the wallet first.
Backup and recovery seed phrase support
If your hardware wallet gets misplaced, stolen, or damaged, you can restore funds with a 12- to 24-word recovery seed.
Wide coin/token and blockchain compatibility
Ensure the wallet you choose supports the cryptocurrencies and chains you currently use to lengthen the time you can use the wallet.
Firmware updates & open security architecture
Regular updates, audit (ideally open-source firmware), and secure boot processes will provide ongoing assurances that a wallet’s security is sufficient.
Passphrase / extra security layers
Having a default passphrase, PIN, or other layers of optional security will aid in the case that the wallet is compromised.
Tips to Keep Your Crypto Safe
Buy Only from Official Sources
Get hardware wallets straight from the manufacturer or authorized partners to prevent purchasing tampered or counterfeit products.
Never Share Your Recovery Phrase
Your 12- to 24- word recovery seed is the ultimate key to your crypto. Do not share it or save it digitally.
Use a Strong PIN or Passphrase
A secure PIN is mandatory and an optional passphrase can offer additional defense in the scenario where someone gets your device.
Store Recovery Phrase Offline
Your recovery phrase must be saved on card, etched on superior metal plates, and kept in a secure location, which is also fire and water safe.
Update Firmware Regularly
Regularly improve your device to meet set standards to fix vulnerabilities and improve compatibility.
Avoid Connecting to Unknown Devices
Limit your hardware wallet to connections with safe computers or clean mobile devices for slander and malware.
Verify Transactions on the Device Screen
All address and transaction details must be verified on the hardware wallet, and the details should NOT be kept on the computer.
Employ Multi-Factor Security
Combine your hardware wallet with additional safeguards like 2FA and biometric measures.
Common Mistakes to Avoid
Purchasing From Unverified Sellers
Ordering hardware wallets from unofficial sites or third parties can lead to receiving a device that has been tampered with or counterfeit.
Saving Recovery Phrase Online
Storing your seed phrase in notes apps, photos, or any cloud service makes it susceptible to hacking.
Ignoring Firmware Updates
Neglecting to update your device firmware can lead to security issues and incompatibility concerns.
Using Weak PINs or No Passphrase
Guessing simple and repetitive PINs is a piece of cake, so make sure your PIN or passphrase is strong and unique.
Connecting to Infected Devices
Infected devices, such as computers, can compromise the transactions of your wallet.
Sharing Recovery Phrase for “Support”
If you are asked for your seed phrase by “support” or “customer service,” this is a scam. No real service will ask you for that.
Not Verifying Transaction Details
Always check the wallet screen for the transaction address and amount instead of solely your computer screen.
Neglecting Physical Security
Keeping your hardware wallet in a easily accessible position increases your chances of losing it or it being stolen.
Losing Backup Without Redundancy
Not storing several secure backups of your recovery phrase may cause you to lose your funds forever if your device breaks.
Overlooking Compatibility Before Purchase
Not all wallets support all coins or blockchains. Ensure the asset you’re transferring will be accepted by the wallet.
Pros and Cons of Using Hardware Wallets
| Pros | Cons |
|---|---|
| Offline Security: Keeps private keys completely offline, protecting against online hacks and malware. | Higher Initial Cost: More expensive than software wallets or exchange storage. |
| Full Ownership: Users have complete control over their crypto assets without relying on third parties. | Learning Curve: Beginners may find setup and operation slightly complex at first. |
| Protection from Phishing & Exchange Hacks: Transactions must be verified physically on the device. | Physical Loss or Damage Risk: Losing the wallet or seed phrase can lead to permanent loss of funds. |
| Multi-Currency Support: Most hardware wallets support a wide range of cryptocurrencies. | Less Convenient for Daily Trades: Requires manual confirmation for each transaction. |
| Secure Backup Options: Recovery phrases allow wallet restoration even if the device is lost. | Firmware Update Required: Users must regularly update firmware to stay protected. |
| Tamper-Resistant Design: Devices like Ellipal Titan and SafePal S1 feature anti-tampering and self-destruct systems. | Limited Mobile Compatibility (Some Models): Not all wallets connect easily with smartphones. |
Future of Crypto Security and Wallet Technology
As time passes, cryptocurrencies, wallets, and wallets become more secure. Cybersecurity predictions become more precise. Blueprints for future hardware wallets. Hardware wallets focus on making self-custody with wallets more secure, personal privacy, self-verifying self-custody accounts, and auxiliary biometric safeguards.
Artificial intelligence in threat detection will provide safeguards for automated fraudulent transaction prevention. Automated wallet creations for autonomous DeFi, NFTs, and Web3 decentralized applications secure interactions with decentralized ecosystems.
Future hardware wallets facilitate air-gapped operations, encrypted backups, and multi-signature accounts for self-custody accounts. These features enable unrestricted access for institutional investors.
Conclusion
To sum up, in 2025, one of the safest and smartest moves you can make is to secure your crypto with the best hardware wallets. These devices keep your private keys offline, in your possession, and beyond the reach of hackers and other online dangers.
Advanced models such as the Ledger Nano X, Trezor Model T, or Ellipal Titan 2.0, offer high discounts and uniquely designed security features protecting your digital wealth.
Safe innovations over setup, storage, and maintenance, will keep your crypto safe, allowing you to confidently invest digitally while enjoying mental peace.
FAQ
What should I do if my hardware wallet gets damaged?
You can simply buy a new device and restore your crypto using your recovery seed phrase, as long as it’s kept safe.
Can I store multiple cryptocurrencies in one wallet?
Yes. Most modern hardware wallets, like Ledger and SafePal, support hundreds of cryptocurrencies and tokens, allowing you to manage all your assets in one device.
How often should I update my hardware wallet?
You should regularly update your wallet’s firmware to patch vulnerabilities, improve performance, and ensure compatibility with new coins.








